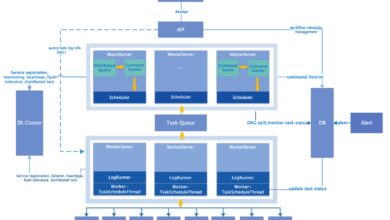
System Group: 7 Powerful Insights You Need to Know Now
Welcome to a deep dive into the world of system group—a concept reshaping how organizations, tech infrastructures, and collaborative networks operate today. Whether you’re in IT, management, or engineering, understanding system group dynamics is essential for efficiency, security, and innovation.
What Is a System Group? Defining the Core Concept

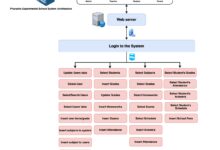
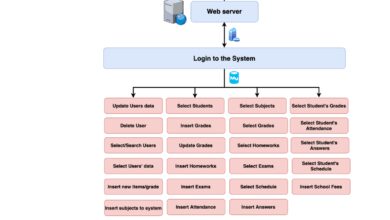
The term system group appears across various domains—operating systems, enterprise software, network administration, and organizational theory. At its core, a system group refers to a structured collection of components, users, or processes that function collectively within a defined system to achieve specific objectives.
Origin and Evolution of the Term
The concept of a system group traces back to early computing systems in the 1960s and 1970s, when multi-user operating systems like UNIX began implementing user groups to manage permissions and access control. These groups allowed system administrators to assign rights collectively rather than individually, streamlining security and resource allocation.
Over time, the idea expanded beyond computing. In organizational behavior, a system group might refer to interdependent teams working within a larger corporate structure. In systems theory, it denotes subsystems interacting within a broader framework—such as departments in a hospital or modules in a software suite.
Types of System Groups Across Domains
Different fields interpret and apply the system group concept in unique ways:
- IT and Cybersecurity: User groups in Linux or Windows Active Directory that control file access and administrative privileges.
- Software Architecture: Microservices grouped into functional clusters (e.g., authentication group, payment processing group).
- Organizational Management: Cross-functional teams operating as cohesive units within a company’s operational system.
- Industrial Engineering: Machine groups in manufacturing systems that perform related tasks on an assembly line.
Each variation maintains the foundational principle: a system group enhances coordination, reduces redundancy, and improves system-wide performance.
“A system is more than the sum of its parts; a system group is the glue that binds those parts into a functioning whole.” — Adapted from Ludwig von Bertalanffy, founder of General Systems Theory
The Role of System Group in Operating Systems
In computing, one of the most concrete applications of a system group is within operating systems. Here, system groups are critical for managing user permissions, securing data, and enabling efficient administration.
Linux and Unix: The Birthplace of System Groups
In Linux and Unix-based systems, every user belongs to one or more groups. These groups determine access rights to files, directories, and system commands. For example, members of the sudo group can execute administrative commands, while the www-data group controls web server processes.
System groups in Linux are defined in the /etc/group file, which lists group names, IDs (GIDs), and member users. This centralized management allows administrators to enforce policies at scale.
Learn more about Linux group management at the Linux Foundation website.
Windows Active Directory and Domain Groups
Microsoft’s Windows operating systems use a more complex model through Active Directory (AD). Here, system groups are part of a directory service that manages users, computers, and resources across a network.
Active Directory supports two main group types:
- Security Groups: Used to assign permissions and manage access control.
- Distribution Groups: Primarily for email distribution, though they can be repurposed.
Groups can be scoped globally, within a domain, or across domains, allowing fine-grained control in enterprise environments. For instance, the Domain Admins group has full control over the domain, while Print Operators can manage printers but nothing else.
Best Practices for Managing System Groups in OS Environments
Effective system group management is crucial for security and usability. Key best practices include:
- Principle of Least Privilege: Assign users only the group memberships they need to perform their jobs.
- Regular Audits: Periodically review group memberships to remove inactive or unauthorized users.
- Naming Conventions: Use clear, consistent names (e.g.,
IT-Admins,Finance-Read-Only) to avoid confusion. - Group Nesting: Use nested groups to simplify management (e.g., a
Managersgroup containing departmental leads).
Tools like PowerShell and Bash scripts can automate group management, reducing human error and improving compliance.
System Group in Enterprise Software and Cloud Platforms
As businesses move to cloud-based solutions, the concept of system group has evolved to fit scalable, distributed environments. Platforms like AWS, Google Cloud, and Salesforce use system groups to manage access, resources, and workflows.
AWS IAM: Identity and Access Management Groups
In Amazon Web Services (AWS), Identity and Access Management (IAM) allows administrators to create system groups with specific policies attached. For example, a Developers group might have read/write access to S3 buckets, while a ReadOnly-Analysts group can only view data.
IAM groups eliminate the need to assign permissions individually, making it easier to onboard and offboard employees. Policies are written in JSON and can be version-controlled, enhancing security and auditability.
Explore AWS IAM documentation at aws.amazon.com/iam.
Google Workspace and Microsoft 365 Group Management
Google Workspace (formerly G Suite) and Microsoft 365 use system groups to manage email distribution, shared drives, and application access. In Google Workspace, administrators can create organizational units and assign groups to them, enabling granular control over services like Gmail, Drive, and Meet.
Microsoft 365 uses Microsoft Entra ID (formerly Azure AD) to manage groups. These can be synchronized with on-premises Active Directory or created in the cloud. Dynamic groups automatically update membership based on rules (e.g., all users in the Finance department).
This automation reduces administrative overhead and ensures consistent access policies across hybrid environments.
Role-Based Access Control (RBAC) and System Groups
Role-Based Access Control (RBAC) is a security model where permissions are assigned based on roles, and system groups represent those roles. For example:
- Role: Database Administrator → Group: DB-Admins → Permissions: Full access to databases
- Role: Customer Support Agent → Group: Support-Tier1 → Permissions: View customer tickets, no deletion rights
RBAC enhances security by minimizing over-provisioning and simplifies compliance with regulations like GDPR and HIPAA. System groups are the backbone of RBAC implementation.
System Group in Organizational Theory and Management
Beyond technology, the idea of a system group applies to human organizations. In management science, a system group refers to a team or department functioning as a subsystem within a larger organizational system.
Synergy and Interdependence in Work Groups
According to systems theory, organizations are composed of interdependent parts. A system group—such as a marketing team or R&D department—contributes to the overall mission through specialized functions.
When these groups work in synergy, the organization performs better than the sum of its parts. However, poor communication or misaligned goals can create bottlenecks or conflicts.
For example, if the sales system group promises features not yet developed by the engineering group, customer satisfaction drops. Coordination mechanisms like cross-functional meetings or integrated project management tools help align system groups.
Formal vs. Informal System Groups
Organizations contain both formal and informal system groups:
- Formal Groups: Officially recognized teams with defined roles, reporting structures, and objectives (e.g., HR department, IT support).
- Informal Groups: Emergent networks based on social ties, shared interests, or problem-solving needs (e.g., a lunchtime coding club or a mentorship circle).
While formal system groups are documented in org charts, informal ones often drive innovation and employee engagement. Smart leaders recognize and support both types.
Case Study: Toyota’s Production System Groups
Toyota’s renowned production system relies heavily on system groups. Workers are organized into small teams responsible for specific assembly stages. Each group has autonomy to stop the line if defects are detected—a practice known as jidoka.
These system groups are cross-trained, fostering flexibility and accountability. Daily stand-up meetings (kaizen) allow continuous improvement. This model has been replicated worldwide and demonstrates how well-designed system groups enhance quality and efficiency.
Security Implications of System Group Mismanagement
While system groups improve efficiency, poor management can lead to serious security risks. Unauthorized access, privilege escalation, and data breaches often stem from flawed group policies.
Common Security Vulnerabilities
Several vulnerabilities arise from improper system group handling:
- Overprivileged Groups: Users with excessive permissions due to broad group assignments.
- Orphaned Accounts: Former employees remaining in critical groups after leaving the organization.
- Shadow Groups: Unofficial or undocumented groups created outside standard procedures.
- Group Explosion: Too many overlapping groups causing confusion and access conflicts.
A 2023 report by CyberArk found that 74% of data breaches involved misuse of privileged credentials, many tied to group-based access.
Strategies for Securing System Groups
To mitigate risks, organizations should adopt the following strategies:
- Regular Access Reviews: Conduct quarterly audits of group memberships.
- Just-In-Time (JIT) Access: Grant temporary group membership for specific tasks, then revoke it.
- Multi-Factor Authentication (MFA): Require MFA for high-privilege groups.
- Logging and Monitoring: Track group membership changes and access attempts using SIEM tools.
Implementing Zero Trust Architecture further strengthens security by verifying every access request, regardless of group affiliation.
Compliance and Regulatory Requirements
Industries like finance, healthcare, and government face strict regulations requiring proper access controls. For example:
- GDPR: Requires data access to be limited to authorized personnel.
- HIPAA: Mandates role-based access to patient records.
- SOC 2: Audits include reviewing user and group management practices.
System groups must be documented, monitored, and aligned with compliance frameworks. Automated tools like SailPoint or Okta can help enforce policy adherence.
System Group in Software Development and DevOps
In modern software development, system groups play a vital role in CI/CD pipelines, infrastructure as code, and team collaboration.
Team Structure in Agile and DevOps
Agile methodologies organize developers into cross-functional system groups—often called squads or pods. Each group includes developers, testers, and operations engineers, enabling end-to-end ownership of features.
Spotify’s famous engineering model uses “tribes,” “squads,” and “chapters” as system groups to balance autonomy and alignment. This structure fosters innovation while maintaining technical consistency.
Infrastructure as Code and Group Policies
Tools like Terraform, Ansible, and Puppet allow system groups to be defined and deployed programmatically. For example, a Terraform script can create an AWS IAM group with specific policies, ensuring consistency across environments.
This approach eliminates configuration drift and supports version control, making audits and rollbacks easier. Infrastructure as code turns system group management into a repeatable, scalable process.
CI/CD Pipelines and Access Control
Continuous Integration/Continuous Deployment (CI/CD) pipelines rely on system groups to control who can trigger builds, deploy to production, or modify pipeline configurations.
For instance, in Jenkins or GitHub Actions, only members of the Deploy-Managers group may approve production deployments. This prevents accidental or malicious changes, enhancing system stability.
Future Trends: AI, Automation, and System Group Evolution
As technology advances, the concept of system group is evolving. Artificial intelligence, machine learning, and automation are transforming how groups are created, managed, and optimized.
AI-Driven Group Management
AI-powered identity governance platforms can analyze user behavior and recommend group memberships. For example, if a new employee frequently accesses financial reports, the system might suggest adding them to the Finance-Analysts group.
These recommendations reduce manual work and improve accuracy. Companies like Microsoft and Google are integrating AI into their identity management suites to enable smarter, adaptive access control.
Dynamic and Self-Organizing System Groups
Future systems may feature self-organizing groups that adapt in real time. In a smart factory, machines could form temporary system groups to handle urgent orders, then disband when complete.
Similarly, in software, microservices might dynamically group based on workload demands, improving scalability and resilience. This shift moves from static, predefined groups to fluid, context-aware collectives.
Decentralized Identity and Blockchain-Based Groups
Blockchain technology enables decentralized system groups where membership and permissions are recorded on an immutable ledger. This is particularly useful in multi-organizational collaborations, such as supply chains or healthcare networks.
For example, a consortium of hospitals could form a system group with shared access to patient records, governed by smart contracts. Each member’s access is verified cryptographically, enhancing trust and security.
How to Optimize System Group Performance
Whether in IT, management, or software development, optimizing system group performance leads to better outcomes. Here are actionable strategies:
Define Clear Objectives and Boundaries
Every system group should have a well-defined purpose, scope, and set of responsibilities. Ambiguity leads to overlap, conflict, or inaction.
Use frameworks like RACI (Responsible, Accountable, Consulted, Informed) to clarify roles within the group. This ensures everyone knows their contribution and limits.
Foster Communication and Collaboration
Effective communication is the lifeblood of any system group. Use collaboration tools like Slack, Microsoft Teams, or Jira to keep members aligned.
Regular stand-ups, retrospectives, and documentation practices help maintain transparency and accountability.
Measure and Improve Continuously
Track key performance indicators (KPIs) relevant to the group’s function:
- For IT groups: Uptime, incident response time, access request fulfillment rate.
- For development groups: Deployment frequency, lead time for changes, bug resolution rate.
- For business teams: Project completion rate, customer satisfaction, cost efficiency.
Use data to identify bottlenecks and implement improvements through iterative cycles.
What is a system group?
A system group is a structured collection of users, processes, or components that operate together within a defined system to achieve specific goals. It is used in computing, organizational management, and systems theory to improve coordination, security, and efficiency.
How do system groups improve security?
System groups enhance security by enabling role-based access control (RBAC), minimizing individual permission assignments, and allowing centralized management of privileges. Regular audits and least-privilege principles further reduce risks.
What are examples of system groups in real life?
Examples include Linux user groups like sudo, Active Directory security groups in Windows, Agile development squads in software teams, and production cells in manufacturing systems like Toyota’s.
Can system groups be automated?
Yes, system groups can be automated using tools like IAM in cloud platforms, infrastructure as code (Terraform, Ansible), and AI-driven identity governance systems that recommend or manage memberships dynamically.
Why is group management important in DevOps?
In DevOps, system groups control access to CI/CD pipelines, production environments, and configuration management tools. Proper group management ensures secure, reliable, and auditable deployments while supporting team autonomy.
Understanding the system group concept is no longer optional—it’s a strategic necessity across industries. From securing user access in operating systems to organizing agile teams and enabling smart factories, system groups are the building blocks of efficient, scalable, and secure systems. By applying best practices in group definition, management, and optimization, organizations can unlock higher performance, reduce risks, and adapt to future technological shifts. Whether you’re a sysadmin, manager, or developer, mastering the dynamics of system groups empowers you to build better systems.
Further Reading: